Overview
This page describes how to Integrate AutoCompose in your LivePerson application.Integration Steps
There are four parts to the AutoCompose setup process. Use the links below to skip to information about a specific part of the process:- Install the ASAPP browser extension on all agents’ desktop (via a system policy or using your company’s existing deployment processes)
- Configure the LivePerson organization centrally using an administrator account
- Setup agent/user authentication through the existing single sign-on (SSO) service
- Work with your ASAPP contact to configure Auto-Pilot Greetings, if desired
Requirements
Browser Support ASAPP AutoCompose is supported in Google Chrome and Microsoft Edge- NOTE: This support covers the latest version of each browser and extends to the previous two versions
| Domain | Description |
|---|---|
| *.asapp.com | ASAPP service URLs |
| *.ingest.sentry.io | Application performance monitoring tool |
| fonts.googleapis.com | Fonts |
| google-analytics.com | Page analytics |
| asapp-chat-sdk-production.s3.amazonaws.com | Static ASAPP AWS URL for desktop network connectivity health check |
- If installing the ASAPP browser extension via Group Policy Objects, set platform policies to have precedence over cloud policies.
- If installing the ASAPP browser extension via Google Admin Console, set cloud policies to have precedence over platform policies. For more on how to check and modify order of precedence, see policy management guides from Google Enterprise.
Integrate with LivePerson
1. Install the ASAPP Browser Extension
Customers have two options for installing the AutoCompose browser extension: A. Group Policy Objects (GPO) B. Google Admin ConsoleA. Install Group Policy Objects (GPO)
Customers can automatically install and manage the ASAPP AutoCompose browser extension via Group Policy Objects (GPO). ASAPP provides an installation server from which the extension can be downloaded and automatically updated. The Customer’s system administrator must configure GPO rules to allow the installation server URL and the software component ID. Through GPO, the administrator can choose to force the installation (i.e., install without requiring human intervention). The following policies will configure Chrome and Edge to download the AutoCompose browser extension in all on-premise managed devices via GPO:| Policy Name | Value to Set |
|---|---|
| ExtensionInstallSources | https://*.asapp.com/* |
| ExtensionInstallAllowlist | bfcmlmledhddbnialbbdopfefoelbbei |
| ExtensionInstallForcelist | bfcmlmledhddbnialbbdopfefoelbbei;https://app.asapp.com/autocompose-liveperson-chrome-extension/updates |
When policy changes occur, you may need to reload policies manually or force restart the browser to ensure newly deployed policies are applied.
B. Install via Google Admin Console
For Google Chrome deployments, customers can install and manage the ASAPP AutoCompose browser extension using Managed Chrome Device policies in the Google Admin console. The Customer’s system administrator must set up the AutoCompose browser extension through the Google Admin console by creating a custom app and configuring the extension ID and XML manifest URL. Through managed Chrome policies the administrator can choose to force the installation (i.e. install without requiring human intervention). In order to have Chrome download the ASAPP hosted extension in all managed devices through the Google Admin console:- Navigate to Device management > Chrome.
- Click Apps & Extensions.
- Click on Add (+) and look for Add Chrome app or extension by ID option.
- Complete the fields using the values provided below. Be sure to select the From a custom URL option.
| Field | Value |
|---|---|
| ID | bfcmlmledhddbnialbbdopfefoelbbei |
| URL | https://app.asapp.com/autocompose-liveperson-chrome-extension/updates |
To ensure that cloud policies are enabled for production environment users in a given organizational unit, locate that group of users by navigating to Devices > Chrome > Settings menu in Google Suite.Ensure the setting Chrome management for signed-in users is set to Apply all user policies when users sign into Chrome, and provide a managed Chrome experience.
- The extension is force-installed in the browser a. Expand the extension icon in the browser toolbar. b. Alternatively, navigate to chrome://extensions/ or edge://extensions/ and look for ‘ASAPP Extension’ c. Alternatively, navigate to edge://extensions/ and look for ‘ASAPP Extension’
- The extension is properly configured a. Click the extension icon and validate that the allowlist and denylist values in the extension’s options are as they were set. b. Alternatively, navigate to chrome://policy and search for the extension policies. c. Alternatively, navigate to edge://policy and search for the extension policies.
2. Configure LivePerson
Before You Begin You will need the following information to configure ASAPP for LivePerson:- The URL for your custom widget, which will be provided to you by ASAPP
- Credentials to login to your LivePerson organization as an administrator
- Add New Widget
- Open the LivePerson website and login as an administrator.
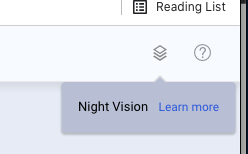
- Go to ‘agent workspace’ and click Night Vision, in the top right:
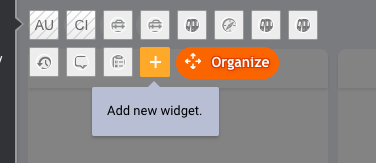
- Click +, then Add new widget.
- Enter Widget Attributes
- Fill in the Widget name as ‘ASAPP’
- Assign the conversation skill(s) to which ASAPP is being deployed in the Assigned skills dropdown menu.
-
Enter the URL that contains the API key you were provided by your ASAPP account contact for your custom widget in the URL field.
When configuring for a sandbox environment, use this URL format:
https://app.asapp.com/autocompose-liveperson/autocompose.html?apikey=\{your_sandbox_api_key\}&asapp_api_domain=api.sandbox.asapp.comWhen configuring for a production environment, use this URL format:https://app.asapp.com/autocompose-liveperson/autocompose.html?apikey=\{your_prod_api_key\}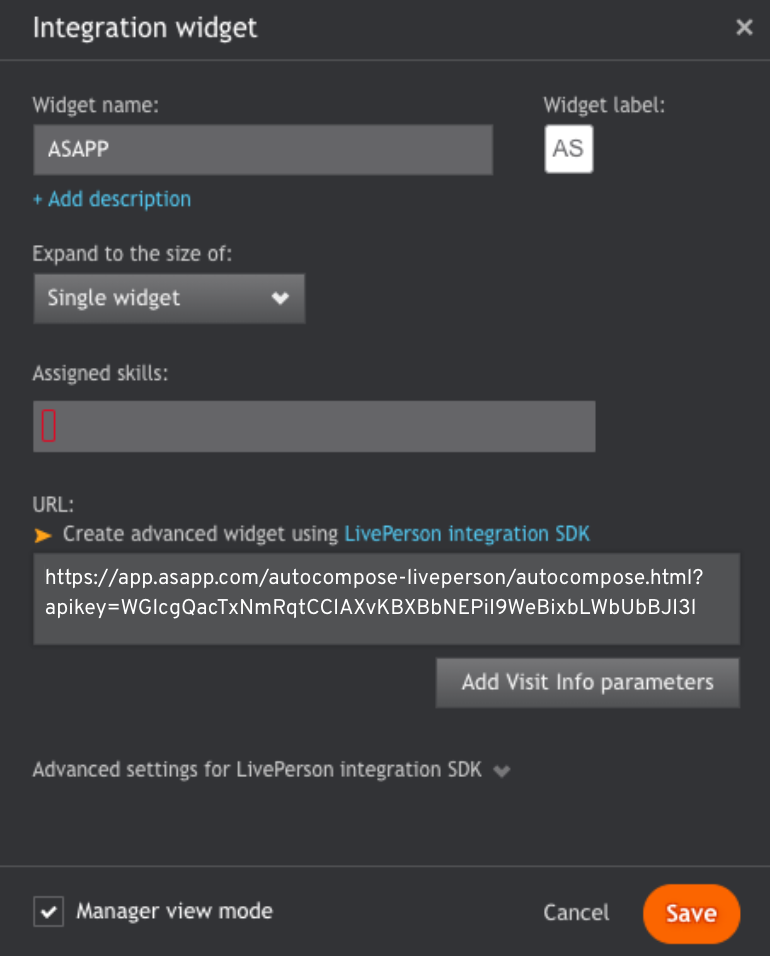
-
Click the Save button.
Ensure Hide and Manager View are unselected once you are ready for agents to see the widget for conversations with the assigned skill(s).
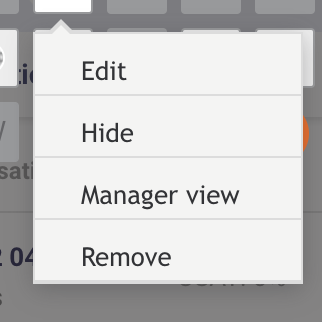
- Move Widget to Top
- Click the Organize button
- Scroll down to the ASAPP widget, and click the Move top button:
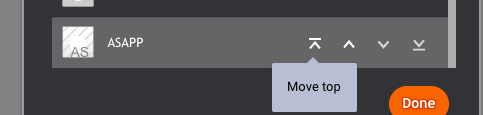
- Click the Done button
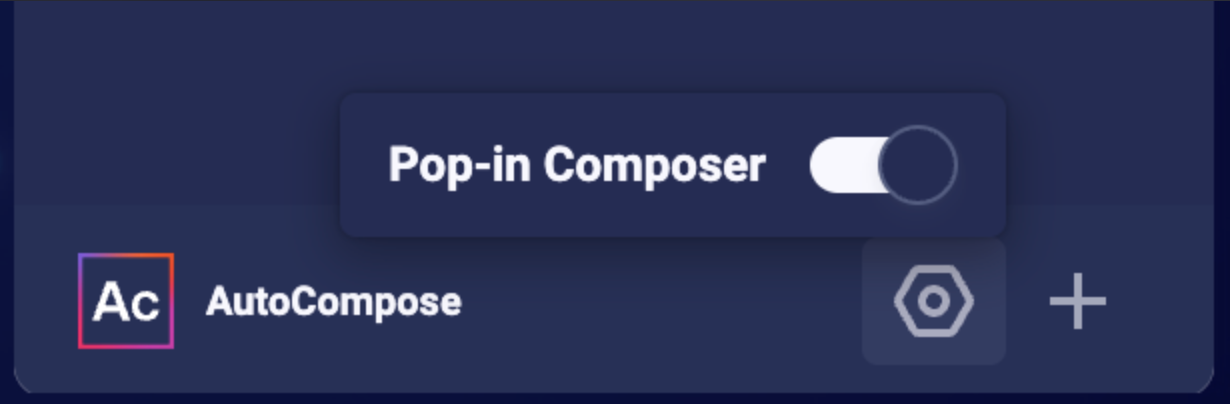
- Enable Pop-in Composer
- In the Agent Workspace, click the nut icon (similar to a gear shape) next to the + icon at the bottom of the AutoCompose panel widget.
- Enable the Pop-in Composer option.
3. Set Up Single Sign-On
ASAPP handles authentication through the customer’s SSO service to confirm the identity of the agent. ASAPP acts as the Service Provider (SP) with the customer acting as the Identity Provider (IDP). The customer’s authentication system performs user authentication using their existing user credentials. ASAPP supports SP-initiated SSO with either OIDC (preferred method) and SAML. Once the user initiates sign-in, ASAPP detects that the user is authenticated and requests an assertion from the customer’s SSO service. Configuration Steps for OIDC (preferred method)-
Create a new IDP OIDC application with type
Web -
Set the following attributes for the app:
*NOTE: ASAPP to provideAttribute
Value*
Grant Type
authorization code
Sign-in Redirect URIs
Production: https://api.asapp.com/auth/v1/callback/\{company_marker\}
Sandbox: https://api.sandbox.asapp.com/auth/v1/callback/\{company_marker\}-sandbox
company_markervalue -
Save the application and send ASAPP the
Client IDandClient Secretfrom the app through a secure communication channel -
Set scopes for the OIDC application:
- Required:
openid - Preferred:
email,profile
- Required:
- Tell ASAPP which end-user attribute should be used a unique identifier
- Tell ASAPP your IDP domain name
- Create a new IDP SAML application.
-
Set the following attributes for the app:
*NOTE: ASAPP to provide
company_markervalue - Save the application and send the Public Certificate to validate Signature for this app SAML payload to ASAPP team
- Send ASAPP team the URL of the SAML application
4. Configure Auto-Pilot Greetings
If you so choose, you can work with your ASAPP contact to enable Auto-Pilot Greetings in your AutoCompose installation. Auto-Pilot Greetings automatically generates a greeting at the beginning of a conversation, and that greeting can be automatically sent to a customer on your agent’s behalf after a configurable timer elapses. Your ASAPP contact can:- Turn Auto-Pilot Greetings on or off for your organization
- Set a countdown timer value after which the Auto-Pilot Greeting is sent if an agent does not cancel Auto-Pilot by typing or clicking a “cancel” button
- Set the global default messages that will be provided for Auto-Pilot Greetings across your organization (note that agents can optionally customize their Auto-Pilot Greetings messages within the Auto-Pilot tab of the AutoCompose panel)
Usage
Customization
LivePerson
For LivePerson, the standard process is to download ASAPP AutoCompose as a standalone widget. In the case that you already have your own LivePerson custom widget, ASAPP also provides the option for you to embed our custom widget inside your own custom widget, thus economizing on-screen real estate. Conversation Attributes Once the ASAPP AutoCompose widget is embedded, LivePerson shares the following conversation attributes with ASAPP: customer name, agent name and skill. ASAPP can use name attributes to populate values into templated responses (e.g. “Hi [customer name], how can I help you today?”) and to selectively filter response lists based on the skill of the conversation. Conversation Redaction When message text in the conversation transcript is sent to ASAPP, ASAPP applies redaction to the message text to prevent transmission of sensitive information. Reach out to your ASAPP account contact for information on available redaction capabilities to configure for your implementation.Data Security
ASAPP’s security protocols protect data at each point of transmission from first user authentication, to secure communications, to our auditing and logging system, all the way to securing the environment when data is at rest in the data logging system. Access to data by ASAPP teams is tightly constrained and monitored. Strict security protocols protect both ASAPP and our customers. The following security controls are particularly relevant to AutoCompose:- Client sessions are controlled using a time-limited authorization token. Privileges for each active session are controlled server-side to mitigate potential elevation-of-privilege and information disclosure risks.
- To avoid unauthorized disclosure of information, unique, non-guessable IDs are used to identify conversations. These conversations can only be accessed using a valid client session.
- Requests to API endpoints that can potentially receive sensitive data are put through a round of redaction to strip the request of sensitive data (like SSNs and phone numbers).