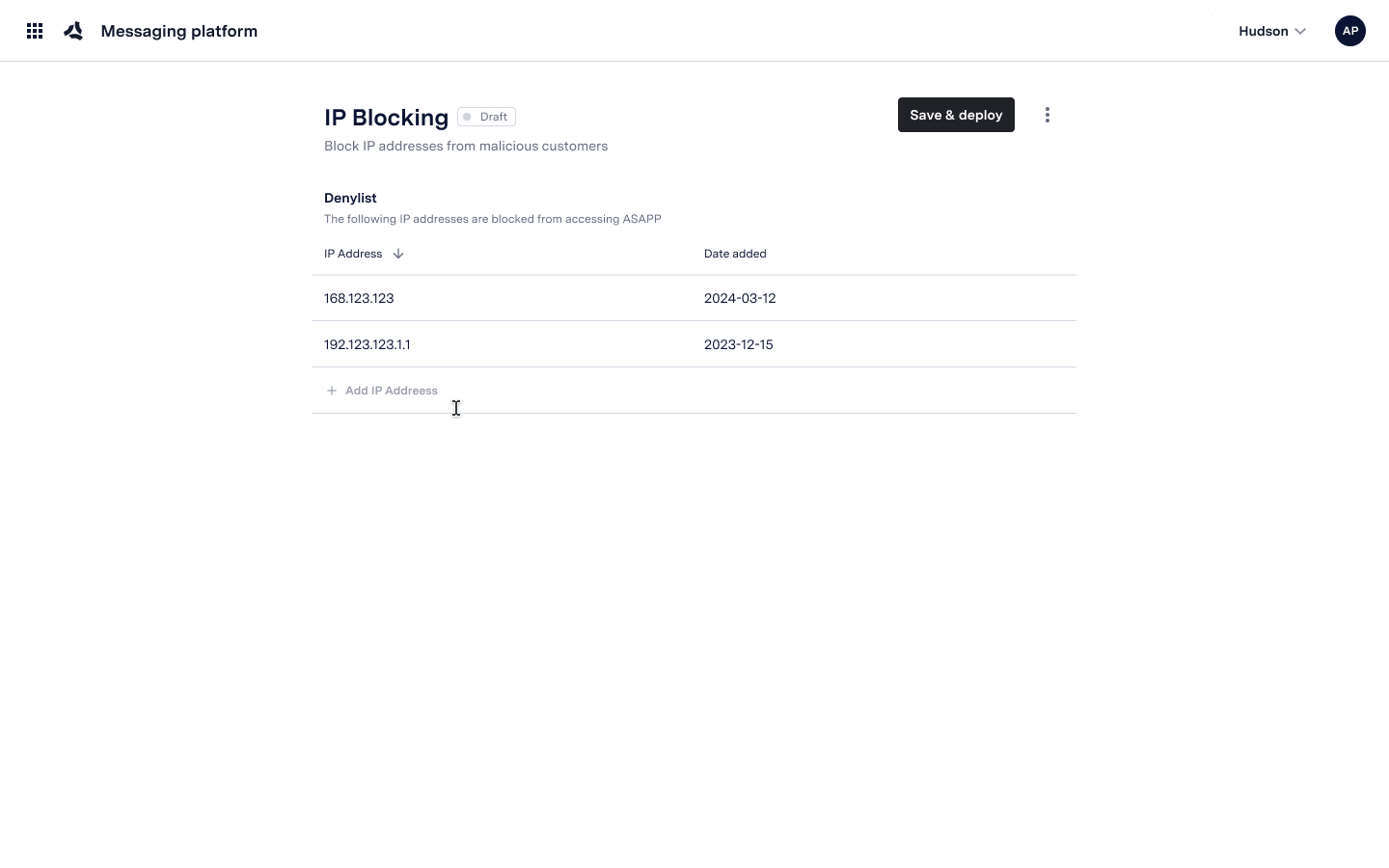
Blocking IP Addresses on AI Console
AI-Console provides the ability for administrators with the correct permissions to block external IP addresses that may present a threat to your organization. To block an IP Address in AI Console:- Manually enter (or copy) an individual IP address in the Denylist
- Click Save and Deploy to save the changes to production
Blocked users receive an error message and the Chat bubble will not appear at the end of their screen.From the API perspective, shouldDisplayWebChat will return a 503 Forbidden error
Additional Contextual Information
Dynamic ISP IP rotates quite often. This means that the 1-1 relationship between a public IP and an individual/device/client is merely temporary and the assignment will continually change in the future as described below. ISP Assignation within the Time IP(1) --- UserA IP(2) --- UserB IP(3) --- UserC … IP(1) --- UserC IP(2) --- UserB IP(3) --- UserA If ASAPP prevents UserA from reaching our platform by blocking IP(1), there is a risk that ISPs assign IP(1) to UserB or UserC at some point in the future. There are also many scenarios where legitimate users share a single IP with abusive users, such as public WiFi networks:- Company named networks
- College or corporate campuses that route many users from a single outbound IP
- Personal and corporate VPN devices that aggregate many uses to a single IP