- A customer identifier
- An access token
- Combination of the conversation history of a customer into a single view to enable the true asynchronous behavior of ASAPP. This allows a customer to come back over time as well as change communication channels but maintain a consistent state and experience.
- Validation of a customer and make API calls for a customer’s data to display to a representative or directly to the customer.
Identification
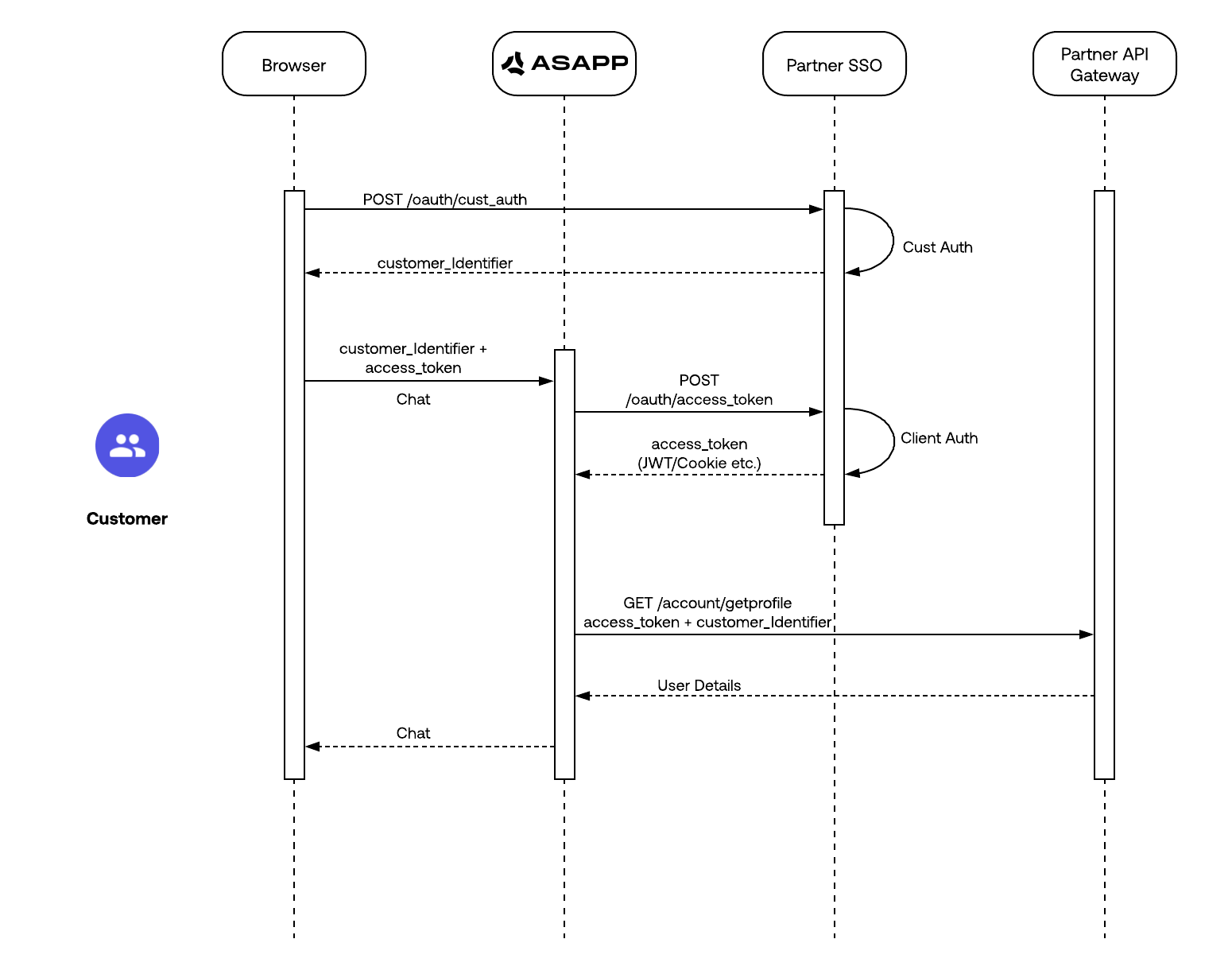
What is a Customer Identifier?
A customer identifier is the first and most important piece of the Customer Authentication strategy. The identifier is the key element to determine:- when to transition from unauthenticated to authenticated
- when to show previous conversation history within chat
Customer Identifier Format
The customer may determine the format of the customer identifier. The ASAPP requirements for the customer identifier are:- Consistent - the same customer must authenticate using the same customer identifier every time.
- Unique - the customer identifier must represent a unique customer; No two customers can have the same identifier.
- Opaque - ASAPP does not store PII data. The customer must obfuscate the customer identifier so it does not contain PII or any other sensitive data. An example of obfuscation strategy is to generate a hash or an encrypted value of a unique user identifier (e.g. user ID, account number, or email address).
- Traceable - customer-traceable but not ASAPP-traceable.
- The customer must be able to trace the customer identifier back to a user. However, it cannot be used by ASAPP, or any other party, to trace back to a specific user.
- The reporting data generated by ASAPP includes the customer identifier. This reporting data is typically used to generate further analytics by the customer. You can use the customer identifier to relate ASAPP’s reporting data back to the actual user identifier and record on the customer side.
Passing the Customer Identifier to ASAPP
Once a customer authenticates a user on their website or app, the customer must retrieve and pass the customer identifier to ASAPP ( typically via the SDK parameters) as part of the conversation authentication flow. You can find more details for your specific integration in the following sections:- Web SDK - Web Authentication
- Android SDK - Chat User Authentication in the Android Integration Walkthrough
- iOS SDK - Basic Usage in the iOS SDK Quick StartiOS SDK
Tokens
While they are not a hard requirement for Customer Authentication, tokens play an important part in the overall Customer Authentication strategy. Tokens provide a way of securely wrapping all communication between Customers, Customer Companies and ASAPP. You can achieve this when you ensure that every request to a server is accompanied by a signed token, which ASAPP can verify for authenticity. Some of the benefits of using tokens over other methods, such as cookies, is that tokens are completely stateless and are typically short-lived. The following sections outline some examples of token input, as well as requirements for their use and validation.Identity Tokens
Identity tokens are self contained, signed, short-lived tokens containing User Attributes like Name, User Identifiers, Contact Information, Claims, and Roles. The simplest and most common example of such a token is a JSON Web Token, JWT. JWTs contain a Header, Payload and Signature. The Header contains metadata about the token, the Payload contains the user info and claims, and the Signature is the algorithmically signed portion of the token based on the payload. You can find more information about JWTs at https://jwt.io/. Example JWT:Bearer Tokens
A Bearer Token is a lightweight security token which provides the bearer, or user, access to protected resources. When a user authenticates, a Bearer Token type is issued that contains an access token and a refresh token, along with expiration details. Bearer tokens are short-lived, dynamic access tokens that can be updated throughout a session using a refresh token. Example Bearer Token:Token Duration
Since every token has an expiration time, you need a way for ASAPP to know when a token is valid and when it expires. A customer can do this by:- allowing decoding of signed tokens.
- providing an API to validate the token.
Token Refresh
You need to refresh expired tokens on either the client side, via the ASAPP SDK, or through an API call. You can find SDK token refresh implementation examples at:- Web SDK - Web Context Provider
- Web SDK - Set Customer
- Android SDK - Context Provider
- iOS SDK - Type Aliases
Token Validation
You need to validate tokens before you can rely on them for API access or user information. Two examples of token validation are:- Compare multiple pieces of information - ASAPP compares a JWT payload against the SDK input of the same attributes, or against response data from a UserProfile API call.
- Signature Validation - ASAPP can also validate signatures and decode data if needed. This would require sharing of a trusted public certificate with ASAPP.